Cyber Resilience in 5G IoT Networks
Internet of Things (IoT) is a term used to describe devices that are essentially small computers with processing capability and sensors or other functions to interact with the outside world. These devices connect together over the Internet or private IP networks to exchange information and form a large and complex distributed system. Traditionally IoT technology has been associated with the “smart home” consisting of lighting, thermostats and home security system functions that are not that critical. But IoT today is much more and has wide application within a large range of industry sectors including manufacturing, healthcare, transport, utilities, mining and warehousing.
The new 5G networks bring major improvements to IoT use cases putting IoT as one of the cornerstones of the 5G business case. There are three major connectivity types for IoT use cases that will benefit from the new features of 5G: massive IoT, broadband IoT and critical IoT.
For massive IoT, the 5G grows the density of supported devices ten to a hundred-fold over the same area. In addition, it includes narrowband IoT (NB-IoT) which is a low-power radio technology for low-speed communication with benefits both in terms of cost and battery-life enabling deployments for use cases such as smart factories, smart meters, fleet management and smart agriculture.
Broadband IoT benefits from the higher throughput speeds of the 5G networks for real-time 4K video use cases for instance, which have use cases in drone-based surveillance, virtual reality applications and self-driving cars.
Critical IoT again are connectivity scenarios where ultra-low latency is needed combined with ultra-reliable data delivery. The 5G networks offers new methods to achieve very low delays and high reliability on the radio interface for use cases such as self-driving cars, robotics, remote surgery and production automation.
Many of the use cases will need two or all three of the connectivity types described above. Consider, for instance, some of the emerging critical communication use cases. Drones are very useful both in public safety scenarios as well as transport and logistics. Control traffic for the drones need critical IoT services, but 4K video feeds utilizing broadband IoT capabilities are as essential as well. And for smart grids, again, control needs critical IoT, but you will also have a large number of sensors in the grid needing massive IoT capabilities.
1. An End-to-End Approach for Cyber Resilience
The benefits of IoT combined with 5G wireless technology is overwhelming and there are many emerging use cases enabled by the 5G networks. But connecting a large number of devices together, sometimes over public networks, which are critical to the business operations brings high requirements on cyber resilience as well. Cyber resilience is concerned with designing the system with an ability to continuously deliver the targeted results, despite of any adverse cyber events. These events could be both intentional cyber-attacks such as denial of service (DoS) attacks or unintentional such as failed configuration changes or software upgrades.
At the core of cyber resilience is cyber security. Cyber security as such is a well-known domain and there are many different models that can be used for cyber security such as the cybersecurity capability maturity model (C2M2), National Institute of Standards and Technology cybersecurity framework (NIST CSF) or the Essential Eight maturity model. Essential parts of these models are backups, operating system and application patching and hardening and proper authentication/authorization, with a focus on the security and resilience of each individual device connected to the network.
But cyber resilience is also a wider concept taking into considerations business continuity and organizational resilience as well. To properly manage cyber resilience, you have to augment the basic cyber security approach with an end-to-end view of security and connectivity as illustrated in the picture below.
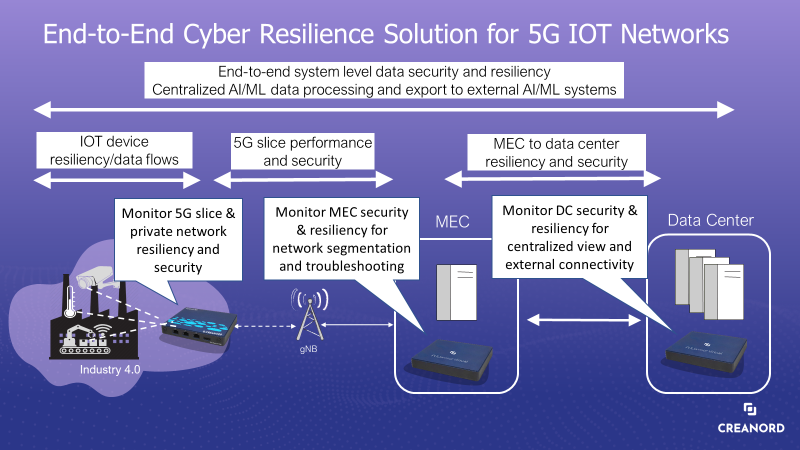
The core idea is that you need to deploy monitoring probes (physical appliances or virtual probes) at three distinct locations in the network to get an end-to-end view of cyber resilience of the system as a whole by monitoring traffic and network at three distinct locations: at the edge of the private network, at the edge computing sites as well as at the data center site. Each one of these locations has very distinct roles in their contribution to the end-to-end view.
2. Edge of the Private Network
At the edge of the private network, the probe will provide a detailed view of mesh connectivity and security for the interconnected IoT devices, whether the wireless technology used is LPWAN, WiFi, 5G or some other wireless technology. The gateway probe ensures that the IoT devices are connected and available, have sufficient network resources available, network is performing as expected and traffic on the network is secure. Furthermore, artificial intelligence and machine learning can be utilized to identify anomalies in the traffic profiles on the network to determine unauthorized access to the network, denial of service attacks and more.
Furthermore, at the edge of the private network we may also monitor the 5G slice performance in order to ensure the resiliency of the 5G slice and to monitor performance of the slice in general. Similar anomaly detection routines for the aggregated traffic on the 5G slice can be performed combined with rogue base station identification and other security measures.
3. Edge Computing Sites
Deploying probes at the edge computing sites (MECs), enables a segmented view of the performance from the private network to the edge computing site as well as between the edge computing site and the data center. The segmented view is helpful both in troubleshooting scenarios as well as getting a detailed understanding of the resilience of the segments. In case of performance challenges or service degradations, you will know whether your performance issues are on the 5G slice segment or between the MEC and the data center.
Also, in terms of the resilience, having a probe at the MEC location enables you to perform available bandwidth monitoring from the MEC towards either the private IOT network or data center. This unintrusive monitoring technique ensure that there is enough bandwidth available on the segment to handle extreme scenarios where there is a sudden increase of traffic on the segment. Knowing how much bandwidth you have available on the segment enables you to proactively increase capacity and make sure your network is resilient in any extreme situation.
4. Data Center Locations
Thirdly, deploying probes in the data center provides you with an end-to-end view of cyber resilience from the data center to the different private IoT networks. It allows you to make sure end-to-end connectivity is performing according to requirements. And, in addition, it also enables you to manage connectivity to external locations in the network that may provide data sources or sinks needed by the IoT devices. It also provides you with a central view to the data flows and the security of the data flows.
Finally, all the data from the edge of the private networks, MEC locations and data centers can be combined to form a deep and thorough view into the cyber resilience of the entire system end-to-end. Flow monitoring at the different locations may detect potential malicious traffic patterns and combined with availability information of the IoT devices, bandwidth anomalies and quality metrics they may filter out false positives and identify weak signals of potential future threats to the cyber resiliency of the system as a whole.
5. Conclusions
Is important for your IT personnel to take up online cyber security degrees to brush up their knowledge and remain on top of emerging changes. As we move on the path to a connected future, cyber resilience is at the core of any of the future IoT networks. Businesses need powerful monitoring software platforms that can provide an end-to-end view of the cyber resilience of the IoT system. PULScore is a powerful network monitoring software platforms that provide you with state of the art probes and tools boosted by innovative ML/AI algorithms to make sure you keep your IoT network up and running in any circumstances. For more information on how Creanord can help you success in deploying future IoT networks, check out our website.